
When evaluating the security of XML based services, one should always consider DTD based attack vectors, such as XML External Entities (XXE) as,for example, our previous post XXE in SAML Interfaces demonstrates.
- XML External Entities (XXE) คือ การใช้งานภาษา XML เวอร์ชันเก่าหรือการตั้งค่า XML ที่ไม่.
- Generate a cheat sheet specific for the technologies your development team used.NET: Manual XML construction Razor (.cshtml/.vbhtml) Web Forms (.aspx) HTML Sanitization SQL - ADO.net SQL - LINQ OS Command LDAP Queries XPath XPath - MvpXml XML parsing (XXE) Java: Coming soon Javascript: Angular Ember.js DOMPurify PHP: Coming soon Python: Coming.
- The OWASP XXE Cheat Sheet instructs users on how to configure security controls for the XML parsers that create JAXB sources to prevent XXE. The following table maps JAXB XML sources to the XML parser that must be configured explicitly with security controls.
The attacks are categorized as follows:
Last updated on 16. January 2019.
Please contact us if you have any missing vectors!
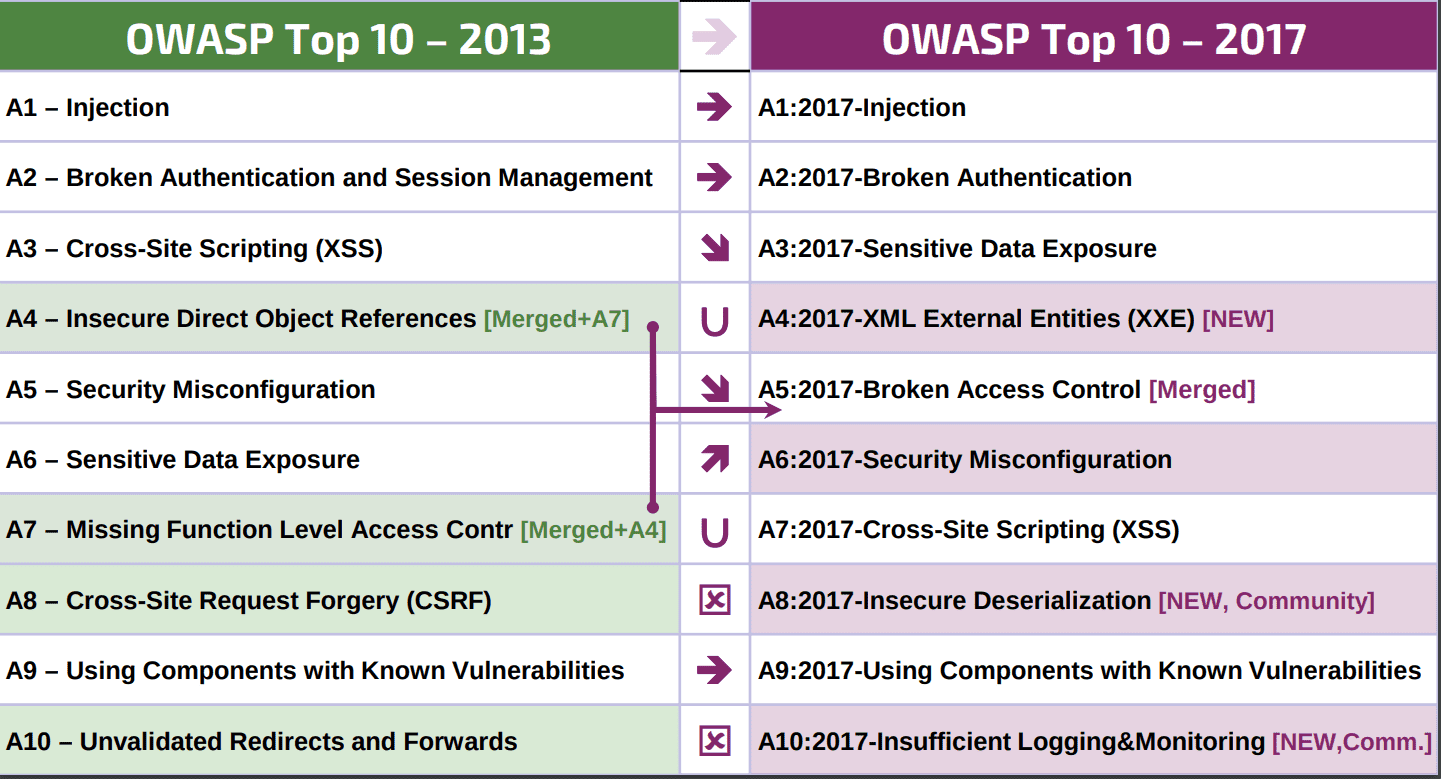
XMLmind XML Editor - Commands Hussein Shafie XMLmind Software Publication date March 5, 2021 Abstract This document contains the reference of all native XXE commands and explains how to write custom macro. XML External Entity Prevention Cheat Sheet¶ Introduction¶. XML eXternal Entity injection (XXE), which is now part of the OWASP Top 10 via the point A4, is a type of attack against an application that parses XML input. XXE issue is referenced under the ID 611 in the Common Weakness Enumeration referential. This attack occurs when untrusted XML input containing a reference to an external.
Testing for Entity Support
If this test is successful and and parsing process is slowed down, there is a high probability that your parser is configured insecurely and is vulnerable to at least one kind of DoS.
Billion Laughs Attack (Klein, 2002)
This file expands to about 30 KByte but has a total of 11111 entity references and therefore exceeds a reasonable threshold of entity references.
Source
Billion Laughs Attack - Parameter Entities (Späth, 2015)
File stored on http://publicServer.com/dos.dtd
Quadratic Blowup Attack
Source
Recursive General Entities
This vector is not well-formed by [WFC: No Recursion].External General Entities (Steuck, 2002)
The idea of this attack is to declare an external general entity and reference a large file on a network resource or locally (e.g. C:/pagefile.sys or /dev/random).However, conducting DoS attacks in such a manner is only applicable by making the parser process a large XML document.
Source
Classic XXE Attack (Steuck, 2002)
We use the file '/sys/power/image_size' as an example, because it is a very simple file (one line, no special characters).
This attack requires a direct feedback channel and reading out files is limited by 'forbidden characters in XML' such as '<' and '&'.
If such characters occur in the accessed file (e.g. /etc/fstab) the XML parser raises an exception and stops the parsing of the message.
Source
XXE Attack using netdoc
Source: @Nirgoldshlager
XXE Attack using UTF-16 (Dawid Golunski)
Some simple blacklisting countermeasures can probably bypassed by changing the default XML charset (which is UTF-8), to a different one, for example, UTF-16The above file can be simply created with a texteditor.
To convert it to UTF-16, you can use the linux tool iconv
# cat file.xml | iconv -f UTF-8 -t UTF-16 > file_utf16.xml
Source, Thanks to @ilmila
XXE Attack using UTF-7
The same trick can be applied to UTF-7 as-well.
# cat file.xml | iconv -f UTF-8 -t UTF-7 > file_utf7.xml
Source, Thanks to @ilmila
This class of attacks vectors is called evolved XXE attacks and is used to (i) bypass restrictions of classic XXE attacks and (ii) for Out-of-Band attacks.
Xxe Cheat Sheet Github
Bypassing Restrictions of XXE (Morgan, 2014)
File stored on http://publicServer.com/parameterEntity_core.dtd
Source
Bypassing Restrictions of XXE (Späth, 2015)
File stored on http://publicServer.com/parameterEntity_doctype.dtd
XXE by abusing Attribute Values (Yunusov, 2013)
This vector bypasses [WFC: No External Entity References].File stored on http://publicServer.com/external_entity_attribute.dtd
Source
Error-based XXE using Parameter Entitites (Arseniy Sharoglazov, 2018)
Abusing local-DTD Files XXE (Arseniy Sharoglazov, 2018)
Contents of sig-app_1_0.dtd
XXE OOB Attack (Yunusov, 2013)
File stored on http://publicServer.com/parameterEntity_oob.dtd
Source
XXE OOB Attack - Parameter Entities (Yunusov, 2013)
Here is a variation of the previous attack using only parameter entities.File stored on http://publicServer.com/parameterEntity_sendhttp.dtd
Source
XXE OOB Attack - Parameter Entities FTP (Novikov, 2014)
Using the FTP protocol, an attacker can read out files of arbitrary length.File stored on http://publicServer.com/parameterEntity_sendftp.dtd
This attack requires to setup a modified FTP server. However, adjustments to this PoC code are probably necessary to apply it to an arbitrary parser.
Source
SchemaEntity Attack (Späth, 2015)
We identified three variations of this attack using (i) schemaLocation, (ii) noNamespaceSchemaLocation and (iii) XInclude.
schemaLocation
Xxe Cheat Sheet 2020
noNamespaceSchemaLocation
XInclude
File stored onhttp://publicServer.com/external_entity_attribute.dtd
DOCTYPE
External General Entity (Steuck, 2002)
Although it is best to reference a well-formed XML file (or any text file for that matter), in order not to cause an error, it is possible with some parsers to invoke an URL without referencing a not well-formed file.
Source
External Parameter Entity (Yunusov, 2013)
File stored onhttp://publicServer.com/url_invocation_parameterEntity.dtd
Source
XInclude
File stored on http://publicServer.com/file.xml
schemaLocation
File stored on http://publicServer.com/url_invocation_schemaLocation.xsd
Owasp Xxe Cheat Sheet
or use this file
noNamespaceSchemaLocation
Xxe Cheat Sheet
File stored on http://publicServer.com/url_invocation_noNamespaceSchemaLocation.xsd
Source
Authors of this Post
Christopher SpäthChristianMainka (@CheariX)
Vladislav Mladenov
What are XML External Entities (XXE)?
According to OWASP, “An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser. This attack may lead to the disclosure of confidential data, denial of service, server side request forgery, port scanning from the perspective of the machine where the parser is located, and other system impacts.”
Applications and in particular XML-based web services or downstream integrations might be vulnerable to attack if:
- The application accepts XML directly or XML uploads, especially from untrusted sources, or inserts untrusted data into XML documents, which is then parsed by an XML processor.
- Any of the XML processors in the application or SOAP based web services has document type definitions (DTDs) enabled. As the exact mechanism for disabling DTD processing varies by processor, it is good practice to consult a reference such as the OWASP Cheat Sheet 'XXE Prevention’.
- If your application uses SAML for identity processing within federated security or single sign on (SSO) purposes. SAML uses XML for identity assertions, and may be vulnerable.
- If the application uses SOAP prior to version 1.2, it is likely susceptible to XXE attacks if XML entities are being passed to the SOAP framework.
- Being vulnerable to XXE attacks likely means that the application is vulnerable to denial of service attacks including the Billion Laughs attack.
XXE Examples
Numerous public XXE issues have been discovered, including attacking embedded devices. XXE occurs in a lot of unexpected places, including deeply nested dependencies. The easiest way is to upload a malicious XML file, if accepted:
Example #1: The attacker attempts to extract data from the server
Example #2: An attacker probes the server's private network by changing the above ENTITY line to
Example #3: An attacker attempts a denial-of-service attack by including a potentially endless file
